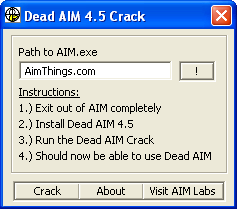
Padillac’s aim bump v1
Remote Aim Away State [Read Me]
Remote Aim Away State: version 0.9.5 By Menace
About:
————-
This program is a Beta version. I made it for myself at college, and found it quite useful.
I don’t really feel like working on it anymore so if anyone wants to add stuff or work
on it I will gladly give you the source code.
Problems, errors, compatability issues, suggestions, help, programming help, and comments:
Email: wacke973@hotmail.com
*** Look for a Final releases as soon as I get some feedback! ***
Requirements:
————-
-Aim 5+
-Tested w/WinXP
-Works w/ DeadAIM!!! (Tabbed and un-tabbed windows)
How to use:
————-
1) Close all open IM windows
2) Have your away message up and do not check “Hide windows while I’m away”
3) Press Start
Akron Prodigy’s Death as Mysterious as His Short Life RJ2 Ryan Johnson
PPN – Concepts of Echelon by Phonetap – November 07, 1999
Hackers’ Excellent Adventures
by WILLIAM BASTONE
In fact, huddled over his Toshiba laptop, with rock music blaring from his bedroom stereo and Jerry Springer flickering on the TV, the Sheepshead Bay resident looks like any other teenager, albeit one experiencing maximum sensory overload, 1998-style.
But actually Gilson is part of a nationwide networkof teenage computer hackers who have stolen everything from Internet accounts to credit card numbers, a cybergang that has flourished despite a yearlong effort by the FBI to curb this online piracy, the Voice has learned. “I’ve stolen accounts and stuff like that. I didn’t even think it was that big of a deal,” Gilson said. “Everybody does it.”
For months, federal investigators have been serving subpoenas and search warrants at the homes of these young hackers, carting away computers, disks, modems, and other items as parents watch in horror. Agents with the FBI’s computer crimes squad have recently raided homes across the metropolitan area–from Brooklyn to the New Jersey suburbs–as part of a probe into wide-scale credit card fraud and other cybercrimes.
In several instances, agents visited the same residences more than once — first in mid 1997 and then again earlier this year — because some young hackers were undeterred by the federal probe. According to one court record, a hacker recently boasted to a friend that “nothing could be done to him because he was a minor.”
One federal investigator acknowledged that while “it’s tough to prosecute a juvenile,” the FBI is “not always sure you’re gonna find a teenager” at “the end of the string.” The source added, “And if you do, it still doesn’t mean the game is off, because if the damage is severe enough it is still a crime and it’s still a problem.”
Since the probe is ongoing–and every target appears to be underage —
investigators have tried to keep details of the case confidential, including whether any teenagers have been arrested on federal charges. But interviews with several subjects of the criminal inquiry and a confidential FBI document obtained by the Voice provide a detailed look at the current investigation.
The federal probe began last spring, when agents learned of the “massive deployment of a password-stealing program” on the Internet, according to the FBI document. The scheme targeted accounts on America Online (AOL), the nation’s largest online service. AOL is a favorite nesting place for young hackers, who congregate in chat rooms with names like Dead End and Island 55. “Fifteen seems to be the preferred age for an AOL hacker,” said one long-in-the-tooth 18-year-old hacker.
MR Tokens
Rant | 1999
Inside Warez Part #2
Subj: Fwd: º^º^( InSide WaReZ Issue #2 (Part 2)^º^º
Date: 97-07-27 15:22:40 EDT
From: SPYER2000
To: BeAwareX1
Forwarded Message:
Subj: º^º^( InSide WaReZ Issue #2 (Part 2)^º^º
Date: 97-07-27 14:36:05 EDT
From: BuBBLe HoP
«–¥(TRauMaTiZeD MassMailer²·º ßy: ßaNiCKuLa)¥–»
«–¥(This one is Dedicated to TaSHa, BaNiCKuLa’s True Love!)¥–»
«–¥(This Mail took 17.41797 Seconds to send)¥–»
«–¥(There are 69 out of 73 people on the MM)¥–»
«–¥(There have been: 0 Un-Retrievable Mails on This MM)¥–»
«–¥(This is Mail Number: 7 of 19 Mails)¥–»